Federal agencies handle immense volumes of sensitive information—from citizen records to national security intelligence—making them prime targets for increasingly sophisticated cyber threats. With traditional security measures proving inadequate in the face of relentless attacks, adopting a proactive and robust cybersecurity framework is no longer optional but essential.

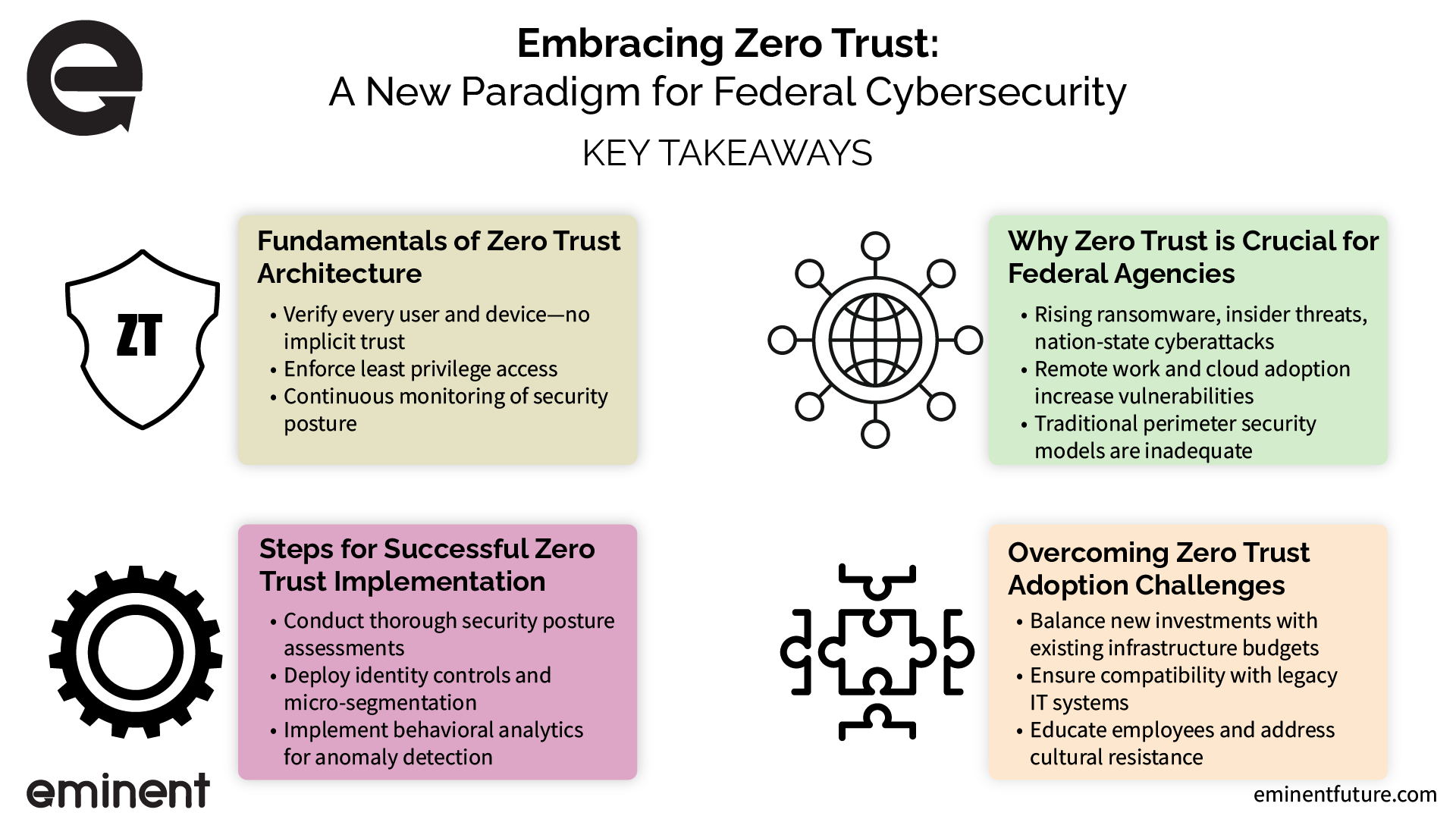
Zero Trust Architecture emerges as the definitive solution, fundamentally transforming federal cybersecurity by eliminating implicit trust within networks. Instead of granting broad access based on assumed safety, Zero Trust continuously verifies every user, device, and transaction, rigorously enforcing stringent access controls to minimize risk.
In this blog, we’ll explore how Zero Trust Architecture enhances federal cybersecurity, empowering agencies to protect their critical data effectively through continuous verification, reduced vulnerabilities, and strict access management.
Understanding Zero Trust Architecture

To effectively implement Zero Trust, it’s critical to grasp its foundational principles:
- Assume No Implicit Trust: Every request, regardless of origin, is verified thoroughly. Trust is never automatically granted.
- Enforce Least Privilege Access: Users and devices are only provided the minimum access necessary to perform their tasks, significantly reducing potential exposure.
- Continuously Monitor and Validate Security Posture: Ongoing evaluation of user behavior, device health, and access patterns ensures that threats are promptly identified and addressed.
Key components that support these principles include:
- Identity and Access Management (IAM): Ensuring identities are authenticated and authorized before granting access.
- Network Segmentation: Dividing networks into smaller, isolated segments to prevent attackers from moving laterally.
- Multi-factor Authentication (MFA): Adding layers of security by requiring multiple verification methods before access is granted.
- Continuous Monitoring and Analytics: Utilizing real-time analysis and monitoring tools to detect and respond to security incidents quickly.
The Need for Zero Trust in Federal Cybersecurity
The cyber threat landscape is evolving rapidly, posing increased risks to federal agencies responsible for national security and sensitive data. Cyber threats are becoming more sophisticated and prevalent, including:
- Ransomware Attacks: Increasing frequency and severity threaten critical infrastructure and sensitive information.
- Insider Threats: Malicious or negligent insiders present significant risks, capable of bypassing traditional perimeter defenses.
- Nation-State Cyberattacks: Sophisticated attacks sponsored by foreign governments targeting critical infrastructure and sensitive federal data.
Additionally, the rapid expansion of remote workforces and widespread cloud adoption have broadened potential attack surfaces, further exposing federal agencies to cybersecurity vulnerabilities.
Traditional cybersecurity frameworks, particularly perimeter-based security models, have significant limitations:
- They wrongly assume users within the internal network are inherently safe, creating vulnerabilities attackers exploit.
- Attackers frequently leverage perimeter weaknesses to move laterally within networks, escalating breaches from isolated incidents into severe compromises.
In this context, Zero Trust Architecture is not merely beneficial—it has become an essential strategic shift to ensure federal cybersecurity resilience.
Implementing Zero Trust in Federal Agencies

Implementing Zero Trust effectively requires agencies to methodically assess, adopt, and align with federal cybersecurity directives.
Assessing Current Security Posture: Agencies must begin by thoroughly evaluating their cybersecurity environments, identifying vulnerabilities through risk assessments, and mapping out critical assets alongside user access levels.
- Conduct risk assessments to understand vulnerabilities.
- Map critical assets and associated user permissions.
Key Steps to Adoption: Federal agencies should prioritize implementing critical Zero Trust measures, including:
- Deploying strong identity and access management controls.
- Implementing micro-segmentation to limit attackers’ lateral movement within the network.
- Leveraging behavioral analytics to monitor and swiftly detect security anomalies continuously.
Compliance and Federal Directives: Adhering to regulatory frameworks ensures standardized security enhancements across agencies.
- Follow NIST Zero Trust guidelines for comprehensive cybersecurity approaches.
- Align with Executive Orders mandating stronger cybersecurity practices for federal entities.
Overcoming Challenges in Zero Trust Adoption
Adopting Zero Trust involves addressing several potential challenges that federal agencies commonly encounter:
Budget and Resource Constraints: Federal agencies must carefully balance investment in new security tools against maintaining and supporting existing infrastructure.
- Strategically allocate resources to integrate new technologies gradually.
- Leverage phased implementation plans to manage budgets effectively.
Legacy System Compatibility: Integrating Zero Trust with legacy IT systems poses significant challenges due to outdated architectures and limited flexibility.
- Incrementally update legacy systems to align with Zero Trust principles.
- Utilize middleware and transition strategies to bridge the gap between old and new technologies.
Cultural and Operational Shifts: Successful adoption requires significant cultural and operational changes within federal agencies.
- Educate federal employees regularly on Zero Trust policies and the importance of cybersecurity.
- Proactively address and manage resistance to strict access controls through communication, training, and support from agency leadership.
Best Practices for a Successful Zero Trust Strategy
To successfully implement Zero Trust, agencies should adopt the following best practices:
Continuous Authentication and Authorization: Implement adaptive security models that authenticate and authorize user access based on contextual information and behavior.
Cloud and Endpoint Security Integration: Extend Zero Trust principles comprehensively into cloud environments and endpoint security, ensuring consistent security posture across all digital assets.
Automation and AI in Zero Trust: Leverage automation and machine learning technologies to enhance threat detection and response capabilities and streamline security management processes.
Securing the Future with Zero Trust
As cyber threats grow increasingly sophisticated, Zero Trust Architecture represents a foundational shift toward proactive, resilient cybersecurity. Federal agencies adopting Zero Trust can significantly reduce cyberattack risks, safeguarding critical data and infrastructure. While this transformative approach requires overcoming challenges, such as budgeting, legacy system compatibility, and cultural resistance, the strategic benefits are undeniable. Federal agencies must continually evolve their cybersecurity strategies, incorporating advancements like automation and artificial intelligence, to stay ahead of emerging threats and secure their digital futures effectively.